Virus that lives on USB flash drive. Be careful
Viruses living on a USB stick. Be careful.
Recently, we often hear about viruses spreading mainly through removable usb-drives or, simply put, through flash drives.
I would like to note that the incidence of this infection is almost 80% (and continues to grow) of all cases of seeking help. This explosive growth can most likely be explained by the widespread use of flash drives among the population.
In the context of this article, we will consider the fundamental features of infection through a flash: how exactly the system is infected, how to recognize "by eye" whether a flash drive is infected, and what to do if you nevertheless have caught such an infection.
So, in fact, the mechanism of infection is not very sophisticated, with a few exceptions, of course.
Infection most often occurs at the time of an attempt to view the contents of a flash drive (this can be a double click with the mouse or pressing the highlighted disk icon with the enter key). It was not for nothing that I described the process of opening a flash drive so carefully, almost even in a childish way - the whole "secret of infection" lies in the way of viewing the disc. When you open the disc, "auto-run" or auto-play of the content should work.
ATTENTION! In order for the autoran-virus to infect your system, in some cases, it is enough just that the flash drive is inserted into the USB.
The essence of autorun is as follows. In the root of the infected flash disk, you can find the autorun.inf file, the contents of which (and this is a simple text file) indicates the path to the executable file (the file may also have a .com extension). As a rule, the executable file - and this is our virus - is also located in the root of a flash drive or in a folder that has the attributes "hidden". The autorun.inf file and the executable file usually have the attributes "system", "read-only" and "hidden".
There is a fairly simple and effective way to recognize whether a flash drive is infected or not, but I will make a reservation that each rule has its own unexpected exceptions. One of the easiest ways to detect such infection is to right-click on the disk. The appearance of the first bold item "Autostart" should alert you: most likely, your flash drive is infected:
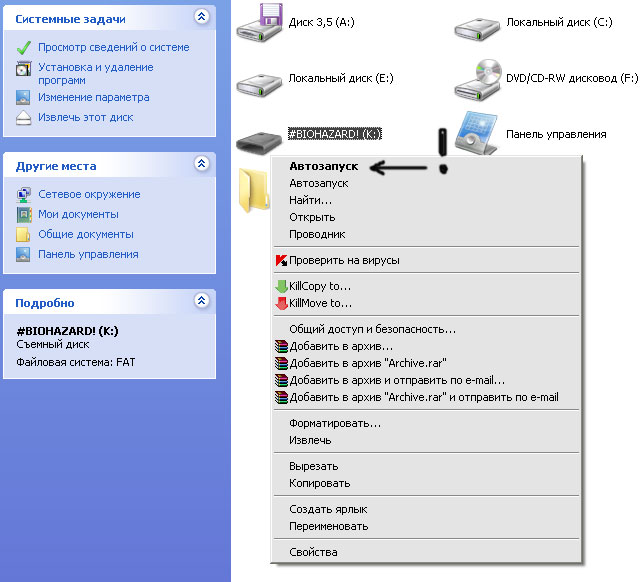
Figure: 1 "Autostart"
Recommended actions in this case:
1) Scan your USB flash drive with an antivirus (although if, when opening the flash, the resident antivirus monitor could not recognize the infection, there is little chance of finding it during scanning)
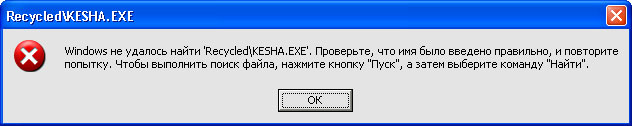
Fig. 2
By the way, it will be said that after being cured by the antivirus, an attempt to open the flash may look as shown in Figure 2. This message is due to the fact that the antivirus, most likely, deleted only the executable file, leaving autorun.inf in its place.
2) Try to remove the infection with your own hands (which we will now do)
In the simplest version, clearing the "alien" means a simple removal of the executable file and the autorun file. In order not to enter the reader into the jungle of the command line, Total Commander may become the most reasonable option for accessing an infected flash drive. Just open the flash "total", set the "Show hidden files" parameters and delete uninvited guests:
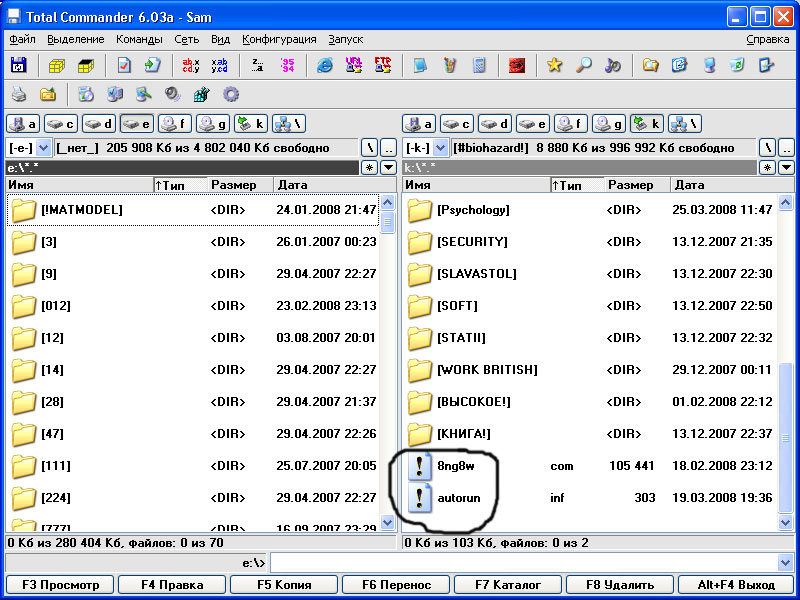
Fig.3 Uninvited guests "right there"
In severe cases, the user may face the following:
The virus will try to deactivate the function of displaying hidden files and folders, which will make it impossible to see the "evil".
Exit: Run Search for files on a USB flash drive, specifying .inf as a template (while not forgetting to set the conditions "search for hidden and system files").
The infected flash drive will look "healthy" (you will not find the bold line "autorun" in the right-click menu). In this case, however, there may be some oddities in the disc menu: incomprehensible hieroglyphs and so on, which also indicates an infection.
It is also possible that the flash menu will be all right, but opening the disk will take a suspiciously long time or an error will pop up when opening - in any of these cases it will not be superfluous to look at the disk for the already mentioned autorun.inf.
And finally, let's look at a live example of one of these viruses (to be more precise Trojans) Kesha.exe, which has already received the status of "people's favorite".
The already familiar autorun.inf with the following content is located at the root of the infected flash disk:
[autorun]
UseAutoPlay = 1
shellExecute = Recycled \ KESHA.EXE
Here on the disk there is a hidden Recycled folder. It contains two files - the executable Kesha.exe and the text file Nosferatu.txt with a rather original "parting word":
Look, and do not believe your eyes.
A black beast lurks in the sky.
I feel trouble in his eyes ...
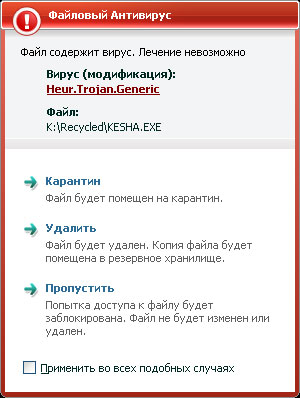
Fig. 4. Kaspersky recognized our "Kesha" as a modification of Heur.Trojan.Generic
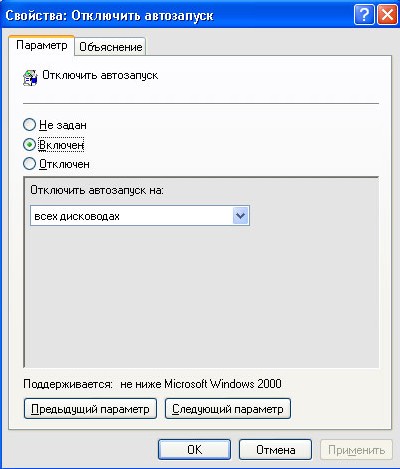
Speaking about an infection transmitted through an autoran, it would be appropriate to recall that there are at least two radical ways to forget about viruses transmitted through a flash drive. One of them is disabling USB support at the hardware level: go to BIOS / select Integrated Peripherals / USB Host Controller / Disabled. It is clear that this method can be used if you do not intend to use a USB flash drive on a local machine. There are other options for protecting against auto-viruses. Why not just disable automatic content launch? For this:
Start / Programs / Accessories / Command line / enter gpedit.msc
In the group policy window that appears, select: Administrative Templates / System / Disable Autostart
Well, that's probably all. Health to you and your computer.
Figure: 5 Disable autorun





 Log in
Log in  Register
Register 